Hurricane
Well-known member
Following a thread from about a year ago, I thought I would write an update.
This was that thread:-
Remote Monitoring - Again.........
This thread not about a replacement for the RUT950 it is about securely connecting the boat's LAN to the home LAN,
In the above thread I found jake009's comments really interesting and challenging.
That thread discusses the Teltonica RUT950 4G router.
Initially, I was very disappointed in the RUT950's internal hardware.
In fact, I still am but I did give it a second go - rewound the firmware to the older version (v6 IIRC ) and it has been working well as a 4G router since.
But, that isn't the point of this discussion.
During that thread/conversation, jake009 commented on my downstream system.
I was using DDWRT routers to connect a secure data tunnel between the boat's LAN and my home LAN
I think jake009's comment at the time was "Thats a Blast from the Past" (referring to my DDWRT routers).
Anyway, that got me thinking - I said so in that thread.
The old system had been running for over 10 years and I decided it needed an upgrade.
I started by experimenting with some Raspberry Pis and OpenWRT.
OpenWRT has loads of support and is still actively being developed.
I also investigated using pfSense and OPNsense but the hardware those projects support is limited and doesn't run on the Raspberry Pi.
All this stuff is Open Source so freely available.
The other attraction for me to OpenWRT is that it is based round Linux (in fact, it IS Linux)
And I'm a great fan of Linux - all my computer systems are Linux or Linux based.
Here is a photo of the Raspberry Pi 4 configured as a router.

After a few weeks playing with the Raspberry Pi 4 and some extra interfaces, Jeff Gerling posted a Youtube video on a couple of other options.
Jeff Gerling is my "go to man" about anything to do with the Raspberry Pi.
He has an excellent Youtube channel - full of information.
BTW, he also manages a second Youtube channel with his farther on industrial radio installations etc - very interesting
Anyway, this is his video on alternatives to my Raspberry Pi 4 as a router:-
So, after digesting that video, I bought a couple of the DFRobot Ethernet router boards and after a lot of searching I managed to aquire a couple of Raspberry Pi CM4s to plug into them.
This is a Raspberry Pi CM4 - they are like "rocking horse poo" to find.

This project ran "on and off" all the way through last year but I finally came back to it as a winter project.
I'm very slow at getting my head round stuff like this - it always takes me a long time to do these kinds of things.
In the meantime, my old DDWRT system was still working so there was no pressing need to upgrade - why mend something that isn't broken?
Well, the converse to that is "don't wait until it breaks".
Finally late in November, I got it all working using OpenWRT and (for me) a new security model using Wireguard.
The old DDWRT system uses OpenVPN for its secure tunnel.
OpenVPN uses complicated electronic Certificates and Keys similar to those used when accessing your bank account.
In my case, I created my own Certification Authority making me completely independent.
But setting up these Certificates and Keys up takes ages.
Wireguard is the "new kid on the block" and MUCH easier to set up.
It uses a much simpler system of Public and Private Keys - a set for each end of a connection.
OpenVPN uses a Client - Server concept whereas Wireguard is considered peer to peer although you can consider one of the peers as a server.
I SAID AT THE BEGINNING THIS WAS GOING TO BE GEEKY - YOU WERE WARNED
Anyway, to summarise
The design is a secondary router which is placed downstream in each LAN (one at home and one on the boat).
Any devices connected to these extra routers can communicate with each other securely as though they were on the same network.
Moving on
Just before Christmas, SWMBO and I visited our daughter and son in law who is equally geeky and he showed me some hardware that he had been playing with.
Essentially, he showed me a router made from a conventional "barebones" x86 computer - more powerful than most desktop PCs.
Lots of these have emerged recently since Intel released the base electronics.
Super little boxes so I bought a couple of these:-

The ones that I bought come from China but you can order them on Amazon.
https://www.amazon.co.uk/dp/B0B28RNZPM?psc=1&ref=ppx_yo2ov_dt_b_product_details
I chose the ones with smallest RAM and smallest SSD - way bigger/more powerful than OpenWRT needs.
They say the delivery is about a month but I got them in about 10 days.
It was then an easy job to translate everything that I had learned on the Raspberry Pi onto the powerful little routers.
Here is a graphical drawing that I put together to show the concept - I've removed sensitive information (IP addresses etc) from the drawing:-
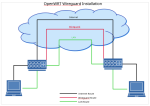
During January I disconnected the old home DDWRT router and inserted my lovely new OpenWRT box.
I then headed out to the boat to connect the other end up.
Usually, when I do this kind of stuff something doesn't work but in this case it all went according to plan.
One small problem - my VoIP telephone connection to home (uses a Raspberry Pi PABX) didn't work.
After a bit of head scratching I found and fixed the problem.
OK - this is a geeky thread so I will explain that problem.
This is for those who know about networks
My old OpenVPN configuration used a TAP connection rather than a TUN connection.
TAP connections operate within a single subnet whereas TUN connections route different subnets.
i.e. with TUN the local LAN is a different address range from the remote LAN.
Wireguard (that I switched to) only works with different subnets (like OpenVPN's TUN)
My VoIP problem was that my VoIP server (the Raspberry Pi PABX) needed to be changed to accept both of the subnets.
Another design problem that I have had to resolve is WOL.
WOL is "Wake On LAN)" - the ability to remotely start/boot a computer.
WOL works using Ethernet Layer 2 (MAC addresses etc).
OpenVPN (TAP) works on Layer 2 so on my old DDWRT system, I could easily send WOL packets to start my devices remotely.
Wireguard is designed to only works on Layer 3 so WOL commands can't transfer through my new tunnel.
The solution is to get the routers themselves to send the WOL packets.
I do this using SSH to run a command on the remote router.
That process isn't very interactive so I wrote some GUI applications to send the WOL commands over SSH.
One GUI application runs on my desktop devices - the other is an Android app.
One additional benefit of a secure tunnel like this is that you can also connect to the system from elsewhere.
For example a PC at another location can also connect into the system.
And all my Android devices can connect wherever/whenever they have an internet connection.
Anyway, I told you this was going to be a geeky thread.
I hope some of you will find this report interesting.
This was that thread:-
Remote Monitoring - Again.........
This thread not about a replacement for the RUT950 it is about securely connecting the boat's LAN to the home LAN,
In the above thread I found jake009's comments really interesting and challenging.
That thread discusses the Teltonica RUT950 4G router.
Initially, I was very disappointed in the RUT950's internal hardware.
In fact, I still am but I did give it a second go - rewound the firmware to the older version (v6 IIRC ) and it has been working well as a 4G router since.
But, that isn't the point of this discussion.
During that thread/conversation, jake009 commented on my downstream system.
I was using DDWRT routers to connect a secure data tunnel between the boat's LAN and my home LAN
I think jake009's comment at the time was "Thats a Blast from the Past" (referring to my DDWRT routers).
Anyway, that got me thinking - I said so in that thread.
The old system had been running for over 10 years and I decided it needed an upgrade.
I started by experimenting with some Raspberry Pis and OpenWRT.
OpenWRT has loads of support and is still actively being developed.
I also investigated using pfSense and OPNsense but the hardware those projects support is limited and doesn't run on the Raspberry Pi.
All this stuff is Open Source so freely available.
The other attraction for me to OpenWRT is that it is based round Linux (in fact, it IS Linux)
And I'm a great fan of Linux - all my computer systems are Linux or Linux based.
Here is a photo of the Raspberry Pi 4 configured as a router.

After a few weeks playing with the Raspberry Pi 4 and some extra interfaces, Jeff Gerling posted a Youtube video on a couple of other options.
Jeff Gerling is my "go to man" about anything to do with the Raspberry Pi.
He has an excellent Youtube channel - full of information.
BTW, he also manages a second Youtube channel with his farther on industrial radio installations etc - very interesting
Anyway, this is his video on alternatives to my Raspberry Pi 4 as a router:-
So, after digesting that video, I bought a couple of the DFRobot Ethernet router boards and after a lot of searching I managed to aquire a couple of Raspberry Pi CM4s to plug into them.
This is a Raspberry Pi CM4 - they are like "rocking horse poo" to find.

This project ran "on and off" all the way through last year but I finally came back to it as a winter project.
I'm very slow at getting my head round stuff like this - it always takes me a long time to do these kinds of things.
In the meantime, my old DDWRT system was still working so there was no pressing need to upgrade - why mend something that isn't broken?
Well, the converse to that is "don't wait until it breaks".
Finally late in November, I got it all working using OpenWRT and (for me) a new security model using Wireguard.
The old DDWRT system uses OpenVPN for its secure tunnel.
OpenVPN uses complicated electronic Certificates and Keys similar to those used when accessing your bank account.
In my case, I created my own Certification Authority making me completely independent.
But setting up these Certificates and Keys up takes ages.
Wireguard is the "new kid on the block" and MUCH easier to set up.
It uses a much simpler system of Public and Private Keys - a set for each end of a connection.
OpenVPN uses a Client - Server concept whereas Wireguard is considered peer to peer although you can consider one of the peers as a server.
I SAID AT THE BEGINNING THIS WAS GOING TO BE GEEKY - YOU WERE WARNED
Anyway, to summarise
The design is a secondary router which is placed downstream in each LAN (one at home and one on the boat).
Any devices connected to these extra routers can communicate with each other securely as though they were on the same network.
Moving on
Just before Christmas, SWMBO and I visited our daughter and son in law who is equally geeky and he showed me some hardware that he had been playing with.
Essentially, he showed me a router made from a conventional "barebones" x86 computer - more powerful than most desktop PCs.
Lots of these have emerged recently since Intel released the base electronics.
Super little boxes so I bought a couple of these:-

The ones that I bought come from China but you can order them on Amazon.
https://www.amazon.co.uk/dp/B0B28RNZPM?psc=1&ref=ppx_yo2ov_dt_b_product_details
I chose the ones with smallest RAM and smallest SSD - way bigger/more powerful than OpenWRT needs.
They say the delivery is about a month but I got them in about 10 days.
It was then an easy job to translate everything that I had learned on the Raspberry Pi onto the powerful little routers.
Here is a graphical drawing that I put together to show the concept - I've removed sensitive information (IP addresses etc) from the drawing:-

During January I disconnected the old home DDWRT router and inserted my lovely new OpenWRT box.
I then headed out to the boat to connect the other end up.
Usually, when I do this kind of stuff something doesn't work but in this case it all went according to plan.
One small problem - my VoIP telephone connection to home (uses a Raspberry Pi PABX) didn't work.
After a bit of head scratching I found and fixed the problem.
OK - this is a geeky thread so I will explain that problem.
This is for those who know about networks
My old OpenVPN configuration used a TAP connection rather than a TUN connection.
TAP connections operate within a single subnet whereas TUN connections route different subnets.
i.e. with TUN the local LAN is a different address range from the remote LAN.
Wireguard (that I switched to) only works with different subnets (like OpenVPN's TUN)
My VoIP problem was that my VoIP server (the Raspberry Pi PABX) needed to be changed to accept both of the subnets.
Another design problem that I have had to resolve is WOL.
WOL is "Wake On LAN)" - the ability to remotely start/boot a computer.
WOL works using Ethernet Layer 2 (MAC addresses etc).
OpenVPN (TAP) works on Layer 2 so on my old DDWRT system, I could easily send WOL packets to start my devices remotely.
Wireguard is designed to only works on Layer 3 so WOL commands can't transfer through my new tunnel.
The solution is to get the routers themselves to send the WOL packets.
I do this using SSH to run a command on the remote router.
That process isn't very interactive so I wrote some GUI applications to send the WOL commands over SSH.
One GUI application runs on my desktop devices - the other is an Android app.
One additional benefit of a secure tunnel like this is that you can also connect to the system from elsewhere.
For example a PC at another location can also connect into the system.
And all my Android devices can connect wherever/whenever they have an internet connection.
Anyway, I told you this was going to be a geeky thread.
I hope some of you will find this report interesting.
Last edited:
